3 minutes
NeverLAN CTF 2020 | RE Writeups
Script Kiddie 100pts
Description:
It looks like a script kiddie was trying to build a crypto locker.
See if you can get the database back?
File:
encrypted_db
This problem gives us the encrypted_db file, you can download it on my github. After that we can see the file format using the following command.
❯ file encrypted_db
encrypted_db: ASCII text
This file has a text format, let’s look at the contents of the file.
❯ cat encrypted_db
.....
764c6d4e7662534973496d466b5a484a6c63334d694f6e7369633352795a
5756300a496a6f69516d396e61584e705932676754576c7a63326c766269
4973496e4e316158526c496a6f69515842304c6941344e4441694c434a6a
61585235496a6f69536d4635626d566962334a760a6457646f4969776965
6d6c775932396b5a534936496a63784e6a4d33496977695a325676496a70
37496d786864434936496a4d7a4c6a45794d6a4d694c434a73626d63694f
.....
After opening the file I thought that it had been encoded into the hex form. I use python2 interactive to decode the contents of the file.
>>> enc = open('encrypted_db', 'r').read().replace('\n','')
>>> dec = enc.decode('hex')
>>> dec
....
....
ZGVyIC0gSmFjb2JpIiwiY2F0\nY2hQaHJhc2UiOiJDdXN0b21pemFibGUgb3B0aW1pemluZyBpbnRlcmZhY2UiLCJicyI6ImUtYnVz\naW5lc3Mgc3ludGhlc2l6ZSBzY2hlbWFzIn19fQo=\n'
As you can see, we get lots of random characters. If we look closer to the last line, there is the character '=' so I’m guessing maybe this is base64. Let’s make a simple code to solve this challange.
❯ nl solver.py
1 import re
2 from base64 import b64decode
3 enc = open('encrypted_db', 'r').read().replace('\n', '')
4 dec = b64decode(enc.decode('hex'))
5 print re.findall(r'flag[^.]*}', dec)
❯ python solver.py
['flag{ENC0D1NG_D4TA_1S_N0T_ENCRY7I0N}']
And we got the flag.
flag{ENC0D1NG_D4TA_1S_N0T_ENCRY7I0N}
Adobe Payroll 100pts
Description:
We've forgotten the password to our payroll machine. Can you extract it?
File:
Adobe_Payroll.7z
Almost the same as the previous challange, in this problem we were given Adobe_Payroll.7z, you can download the file on my github. Let’s extract the 7z file, in the 7z file there are two files, including the executable file and description.md.
❯ file Adobe_Employee_Payroll.exe
Adobe_Employee_Payroll.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
❯ cat description.md
# Adobe Payroll
- Category: I promise it's not malware 😈
- Points: 100
## Description
This is a .NET file. Take a look at dotPeek.
So basically, I think this program uses C# language. So you can use dotPeek to decompile. But in this case I use IDA to do static analysis.
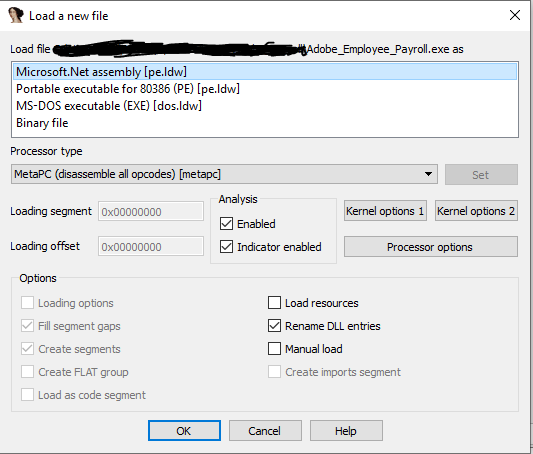
Microsoft.Net assembly [pe.ldw] then click Ok.
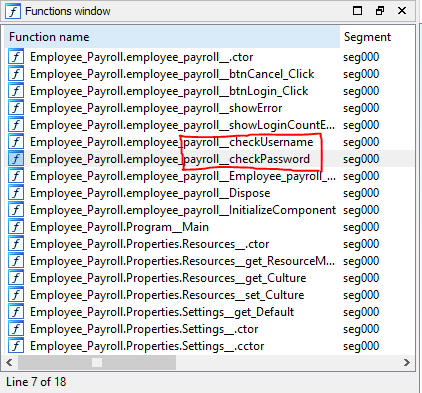
employee_payroll_checkUsername & employee_payroll_chackPassword, That function I think is used to compare a string.
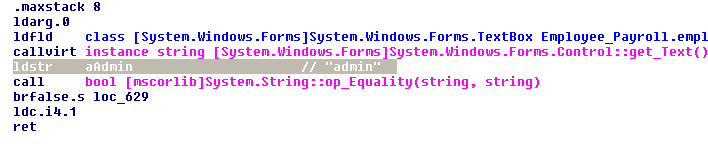
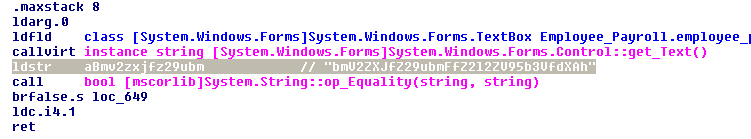
admin as the Username and bmV2ZXJfZ29ubmFfZ212ZV95b3VfdXAh as the Password.
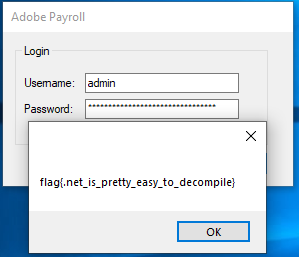
flag{.net_is_pretty_eassy_to_decompile}
Reverse Engineer 300pts
Description:
This program seems to get stuck while running...
Can you get it to continue past the broken function?
File:
reverseng
In this case we are given a binary reverseng file, once again you can check on my github to download the binary file ;). when we try to run the program we will get the SEGV message.
❯ ./revseng
[1] 12675 segmentation fault (core dumped) ./revseng
❯ file revseng
revseng: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=89d54c514d9f6bec697e52edfee4a495266b3577, for GNU/Linux 3.2.0, with debug_info, not stripped
So without further ado let’s get started analyzing it using IDA. There is a function called void __cdecl print () and malloc () function that allocates memory of 0x15 or 21byte to flg, And each byte contains a decimal value. So this is the Pseudocode of the function, after we convert each index value of flg to character.
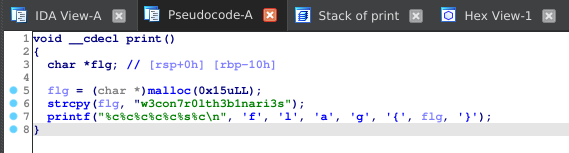
And we get the flag again.
flag{w3con7r0lth3b1nari3s}